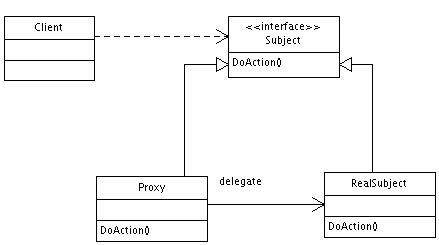
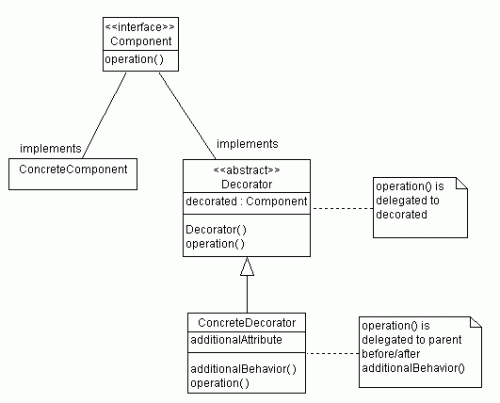
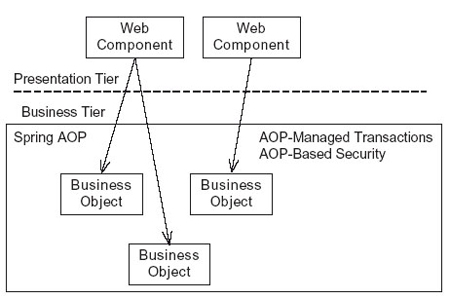
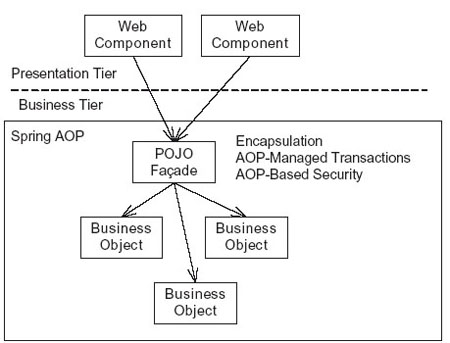
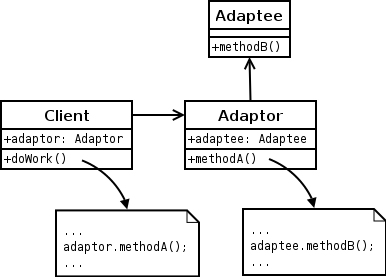
I will graduate in this December, and now looking for a job. To be honest, I really want to be a J2EE programmer. Actually, I have had several interviews with some companies. It doesn’t matter whether I finally get a job, but I have strong feeling that what we learned in the university are not the same things the company want to get from us. When I studied for my bachelor degree in China, I had already hearded a lot of information about the knowledge we get from the classes are detached from the companies. However, now, when I am studying for the masters’ degree in U.S, I find the same thing happens here as in China.
For example, Agile Development is so popular in most software companies currently. However, in the university, we almost have no chance of understanding it deeply, perhaps just heard a little bit informaton on it, and it is not necessary to say we cannot apply it to the real projects.
Whose mistake is this? It is not the professors’ mistake, since they are just responible for giving instructions to students. It is absolutely not the companies’ mistake. They just want to find the right person who can contribute to the companies immediately. It is also not the students’, expecially the good students’, mistake. We spend a large part of our time in all kinds of assignments in that we want a high GPA, so that it is impossible for us to concentrate on the things which are becoming the trend.
In fact, we cannot find the right person who need to be responsible for this problem. What we need to do is finding the reasons caused it and solving this problem. In my opinion, the most important reason is that the purposes of the unversity and the company are different from each other. The universities aim to help the students build solid foundation and form a good learning way, therefore, the students can pick up new things more quickly and effectively in the future. However, the companis hope the new employees can bring their benefits immediately. I think no company would like to invest time and money to the new employees and wait for them to bring profit, which also explains why experience is the most significant factor when somebody is looking for a job. In fact, few days ago, I read an article that some students complain that why the textbooks they use are the ones published 20 years ago, for example, the theory of operating system, which is usually a required course of the computer science department.